The world of cybersecurity doesn’t slow down. If you’re spinning your wheels trying to keep up with the cybersecurity trends for 2025, you’re not alone. This year’s landscape is more unpredictable than ever. But while the headlines might sound overwhelming, understanding the “why” behind these trends empowers you—and your organization—to act, not just react.
From Generative AI supercharging scams to the shadowy risks of unapproved software, let’s break down where the real action is (and where it’s mostly noise). You’ll find practical tips, honest analysis, and facts backed by real experience and credible sources.
Table of Contents
2025 Cybersecurity Trends: Quick Snapshot
In a nutshell: The top cybersecurity trends for 2025 hinge on the rise of Generative AI, the sophistication of deepfakes, looming quantum threats, and the need for smarter authentication. But just as important? The human factor—awareness, oversight, and adaptability.
Generative AI: The Biggest Double-Edged Sword

Q: Why is Generative AI making headlines in cybersecurity this year?
Generative AI makes attacks more personal, adaptable, and frequent—but it also powers smarter defense tools.
Real-World Context:
Last October, one of our clients received an email that mirrored their CEO’s tone perfectly—down to recent speaking points and typical sign-off. The request to transfer sensitive files seemed plausible but was, in fact, crafted by an AI trained on company data scraped from public sources. Fortunately, the finance team had AI-powered anomaly detection in place and flagged it just in time.
Generative AI on Offense
- AI Phishing: Nearly invisible scams tailored to individuals. Messages reference actual meetings, events, and language patterns thanks to AI.
- Malware Creation: Attackers feed known vulnerabilities to AI models and receive near-ready code to misuse—no coding degree required.
Generative AI on Defense
- Threat Intelligence: Security teams use AI to analyze millions of alerts, highlighting the true threats and taking grunt work off analysts’ plates.
- Automation: AI helps write security policies, summarize incidents, and even recommend fixes.
Strengths:
- Rapid threat response and detection
- Rounds-the-clock monitoring with fewer staff
- Smarter security for even small businesses
Concerns:
- AI “hallucinations” can create false positives, overwhelming teams
- Prompt injection attacks trick defensive AIs into making bad decisions
- Shadow AI (users employing unauthorized AI tools) brings new exposure
Deepfakes: Seeing Is No Longer Believing
Q: What’s the real danger with deepfakes in 2025?
Deepfakes make it possible for criminals to fake voices, faces, and even actions—leading to fraud, blackmail, and erosion of trust.
Case Study:
A midsize business in Europe lost $25 million after a finance director joined a video call with their “CFO”—who turned out to be nothing more than a deepfake. The real CFO was bewildered when called to confirm the wire transfer an hour later.

Spotting and Managing Deepfake Threats
- Watch for irregular facial expressions, delay in mouth movement, or odd lighting.
- Always confirm major requests (especially those involving money) offline, regardless of apparent sender.
Strengths:
- Training programs help employees stay vigilant
- Detection tools are improving (though imperfect)
Gaps:
- Open-source deepfake creation tools are widely accessible—even to non-experts
- Attackers move faster than detection tech can keep up
Quantum Computers: The Next Big Disruptor
Q: Should you worry about quantum computers breaking encryption?
Not for everyday data—yet. But attackers are archiving sensitive info today, hoping to decrypt it once quantum computers are ready.
Industry Snapshot:
National agencies and major enterprises are racing to adopt quantum-safe cryptography to protect trade secrets and private records. Backlogged legacy systems, though, are slow to change.

What’s Quantum-safe Cryptography?
These are cryptographic algorithms designed to resist attacks from quantum computers. The US NIST and global agencies are publishing new standards, but migration takes planning and investment.
Strengths:
- Clear industry collaboration on quantum standards
- Early adoption efforts reduce long-term risk
Challenges:
- Upgrading decades-old infrastructure is labor-intensive
- Short-term costs deter leaders who see “quantum” as a distant concern
If you want to learn more about Cybersecurity trends for 2025, you can visit mindjournal.co, gogonihon.jp.net or techbullion.in
AI Phishing: Smarter, Scarier, Harder to Catch
Q: How does AI phishing differ from old-school scams?
Today’s attacks mimic real conversation styles, mention true company events, and are nearly impossible to spot with the naked eye.
Scenario:
An executive assistant receives an urgent Slack from the CFO (or so it seems), referencing yesterday’s board meeting and requesting a confidential report. The language and context perfectly fit. If not for an AI-driven anomaly alert, this would have been a costly mistake.
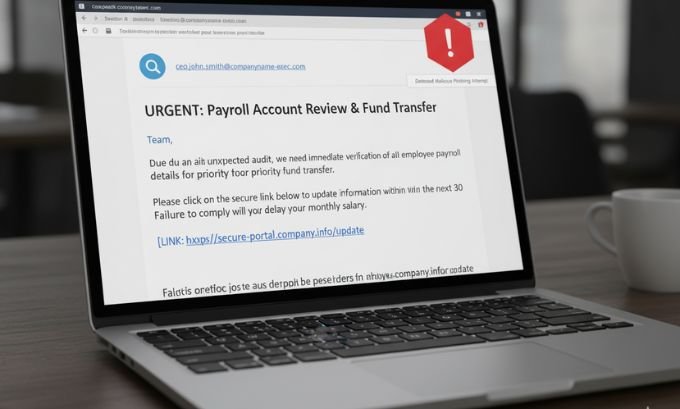
Defense Strategies
- Roll out AI-based anti-phishing software that learns communication patterns
- Require voice or in-person confirmation for sensitive requests
The Risk of Shadow AI
Q: What is Shadow AI and how does it impact cybersecurity trends for 2025?
Shadow AI is any unsanctioned AI usage—think employees turning to public AI chatbots or code tools to speed up tasks, often without security vetting.
Why It Matters:
Private business data or client information can end up on servers you can’t audit or secure. These back doors multiply risks for every “helpful” AI tool added off the radar.
Mitigation Approaches
- Invest in regular software audits
- Train employees on the risks and company policy for third-party AI
Smarter Multi-factor Authentication in 2025
Q: Is your MFA really secure?
Not necessarily. SMS-based MFA is vulnerable to SIM swapping and interception. Experts recommend moving to app-based or biometric authentication.
Comparison Table: Today’s MFA Tools
| MFA Type | Security | User-friendliness | 2025 Verdict |
|---|---|---|---|
| SMS Codes | Low | High | Outdated |
| Authenticator Apps | Medium | Medium | Acceptable |
| Hardware Tokens | High | Medium/Low | Ideal for critical systems |
| Biometrics/Passkeys | High | High | Top Choice |
Whether you’re looking to purchase quality products online in Japan at TokyoMart.store or need expert help growing your brand’s digital presence with LinkLuminous.com, these two platforms offer trusted solutions for shoppers and business owners alike.
DDoS Attacks: Ubiquitous and Cheap
Q: Why are DDoS attacks so prevalent now?
DDoS-for-hire services are rampant. Anyone with a few dollars can knock websites offline, and attacks are both more frequent and larger than ever.
Example from the Field:
Cloudflare reported a 350% rise in DDoS attacks as of Q1 2025. Attacks disrupt midsize businesses, e-commerce sites, and even local government services.
How to Respond
- Use managed DDoS mitigation
- Run tabletop exercises to practice incident response
The Good and Bad of Open-source Code
Q: Is open-source software a cybersecurity risk?
It can be—almost all software now includes open-source components, and vulnerabilities are rapidly weaponized.
Practical Note:
Synopsys’ 2024 report found over 80% of surveyed codebases included at least one serious vulnerability from open-source code.
Smart Practices
- Use vulnerability scanners and patch quickly
- Maintain a comprehensive software inventory
Quantum-safe Cryptography: Your Futureproofing Checklist
Q: What should you be doing about quantum risks right now?
Begin reviewing cryptography in your business. Adopt quantum-safe encryption for anything with a life expectancy of 5–10 years or more.
Key Takeaways
- The earlier you start, the less you’ll scramble later
- NIST’s recommended algorithms are a reliable starting point
Insights from the Field
After years in cybersecurity consulting, I’ve watched “impossible” threats become routine overnight. I’ve seen passkey adoption save a client from an SMS phishing spree, while another narrowly intercepted a fake deepfake domain transfer. What sets the leaders apart isn’t expensive gear—but relentless curiosity, policy clarity, and the willingness to adapt fast.
Cybersecurity Trends for 2025: Quick Reference Table
| Trend | Core Risk | Strongest Defense | Real Example |
|---|---|---|---|
| Generative AI | Realistic phishing, malware | AI-based defense, training | CEO-style phishing attack |
| Deepfakes | Fraud, reputational damage | Verification protocols | Video call scam |
| Quantum Computing | Encryption broken | Quantum-safe migration | “Harvest now, decrypt later” |
| AI Phishing | Spearphishing | Layered filters, callbacks | Message references last meeting |
| Shadow AI | Data leakage, blind spots | Audits, user education | Unapproved chatbot use |
| MFA | Account compromise | Passkey/biometric upgrade | SIM swap MFA breach |
| DDoS Attacks | Service outages | Cloud mitigation, drills | Hospital site offline |
| Open-source Code | Rapidly exploited bugs | Vigilant patching | Library flaw in supply chain |
| Quantum-safe Cryptography | Futureproofing | Early algorithm adoption | Safe records for decades |
FAQ: Cybersecurity Trends for 2025
1. How do I know which trend really matters for my business?
Evaluate based on your industry, your data sensitivity, and how your team uses technology—what’s critical for a financial firm may not be top priority for a coffee shop.
2. Is it true quantum computers could hack my systems soon?
Not yet for most, but we’re in a transition period. The sooner you update cryptography for critical assets, the better you’ll sleep.
3. Are deepfakes relevant to SMBs, or just big targets?
They’re relevant everywhere. Even small firms have been scammed by fake voice messages and emails from “execs.”
4. Is SMS MFA completely unsafe?
Nearly. Move to app-based, hardware key, or biometric options ASAP.
5. Must I avoid all open-source code for safety?
Not at all. Use it wisely, with regular patching and scanning.
6. Why should I care about Shadow AI if my team is small?
One person using an unapproved AI tool can leak client info or trade secrets. Tighter oversight protects everyone.
Wrapping Up: Your Cybersecurity Approach for 2025
Cybersecurity trends for 2025 point to a future that’s smarter—but also trickier. Tools like Generative AI and Quantum Computers bring incredible power, but they also put new weapons in attackers’ hands. The silver lining? Savvy organizations fight back by planning ahead—investing in training, demanding security from the ground up, and adapting quickly. No tech can substitute for engaged, aware people.
Stay curious. Equip your team. Treat every new “miracle” solution with a grain of skepticism, and watch the basics—because that’s where most attacks still succeed or fail.
About the Author
This guide comes from a cybersecurity professional who’s worked with businesses of every size, helping them upgrade defenses and respond to everything from phishing waves to deepfake scams. Analysis and writing draw from hands-on fieldwork, recent research from NIST, Synopsys, Cloudflare, APWG, and real-life security incidents.
For further insights or customized planning, reach out—securing tomorrow’s data starts with today’s questions.

